In this project based on a real-world scenario, I acted as a DevSecOps Engineer, and I deployed a set of EC2 instances and infrastructure in an automated fashion using Terraform (infrastructure as code — IaC). Also, it was necessary to automate the installation of a specific security agent on all the EC2 instances.
To simplify the process, I installed Terraform in the AWS CloudShell command line, rather than configuring Terraform on my local computer, then uploaded the Terraform files (main.tf and provider.tf) and ran ‘terraform init’ to load the Terraform provider plugins, then ‘terraform plan’ to confirm the resources that Terraform would be deploying, and finally ‘terraform apply’ to execute the provisioning of resources. After Terraform provisioned the infrastructure, I created an IAM role for AWS Systems Manager (SSM) to allow SSM to call AWS services on my behalf and gave the role full access permissions to the Simple Notification Service.
The next step was to configure a new Simple Notification Service (SNS) Topic and Subscription to send a notification email to the DevOps team. I copied the Subscription Amazon Resource Name (ARN) of the topic for use later in the Run Command. I then accessed the DevOps group mailbox and confirmed the SNS subscription before continuing. The AWS System Manager Host Management feature was then used to install the System Manager agents on the EC2 instances in an automated manner.
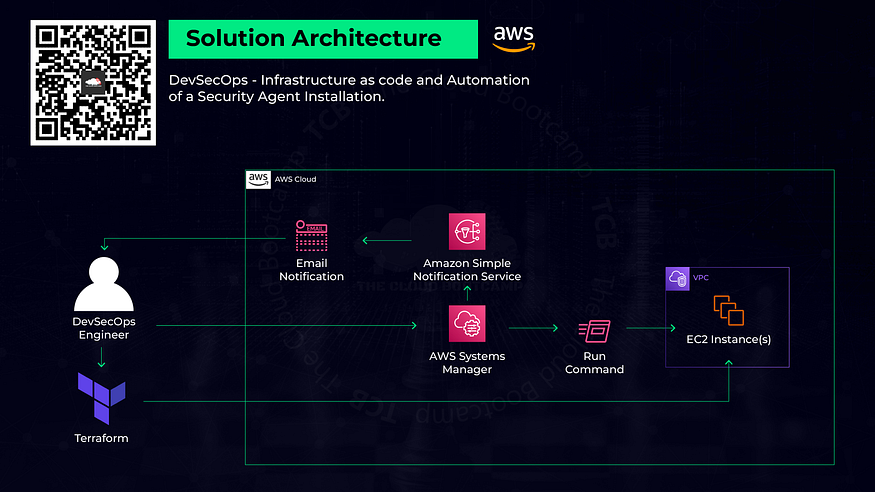
Next, I attempted to use Session Manager to connect to the EC2 instances to view the directory structure prior to deploying the security agents, but I encountered an issue where the EC2 instances were not displayed by Session Manager. I located the following support article:
I performed each of the troubleshooting steps listed in the article, which led to using the cat command on one of the EC2 instances to view the /var/log/amazon/ssm/amazon-ssm-agent.log where I discovered an EC2RoleRequestError. It appears that Systems Manager creates an IAM role, ‘AmazonSSMRoleforInstancesQuickSetup’ which had not been found on the EC2 instance when SSM executed, though the role was present on the EC2 instances when I checked. I rebooted the EC2 instances, and they displayed properly in Session Manager, and I was able to proceed with using Systems Manager and its Run Command feature to create a new command to run a shell script to download and install the security agent on the EC2 instances, configured with an SNS notification set to the IAM role and topic ARN from earlier in the project.
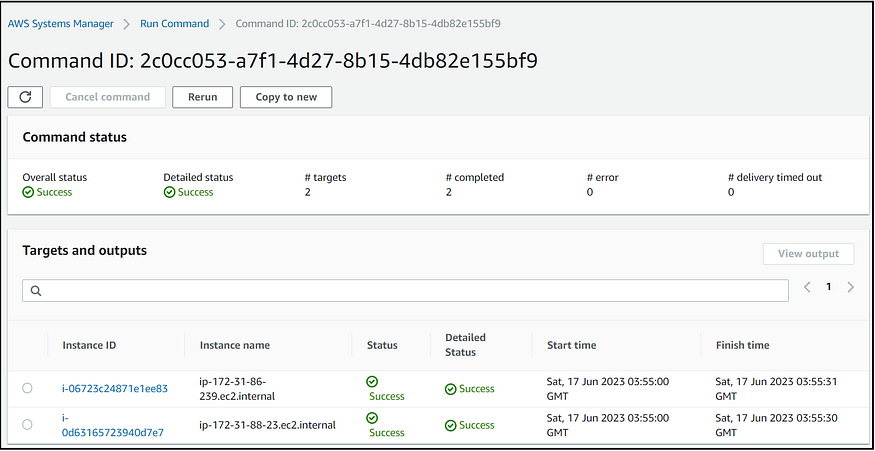
Finally, I executed the run command and confirmed that the DevOps mailbox received several email notifications. I also viewed the Systems Manager Run Command output in the Management Console and reviewed the results of the run command there.
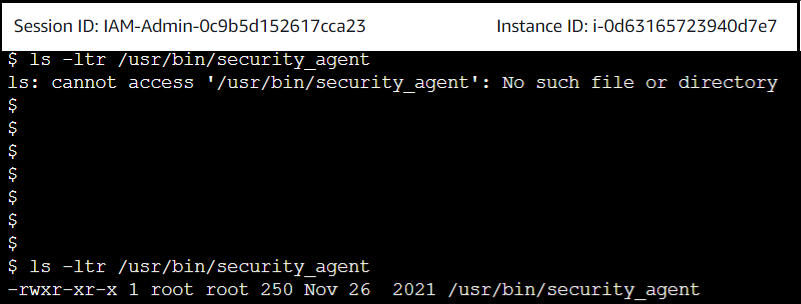
As a final check I used Session Manager to connect to an EC2 instance and confirmed the existence of the security agent installation directory.
I was really impressed by the speed with which Terraform is able to deploy such a large number of resources. Additionally, Systems Manager makes performing system updates to a large number of systems much more efficient that manually connecting to each system to deploy software and updates. The skills I learned in this project will definitely benefit me and the companies I work for going forward.
